Fluency Security is a next generation - cloud based SIEM tool that commands a powerful new approach to managing the cyber health of your company. One that takes feeds from all your security layers, like Mimecast, plus your network and applies advanced analytics, correlating and fusing disparate data, while adding threat intelligence to create an enhanced risk scored record.
Fluency Security strives to substantially reduce false positives while providing sub-second query response times. The critical capability to integrate SOAR functionality is part of our fundamental foundation, such as working with Mimecast and their blocking capability. User behavior analytics provides deep visibility by tying together MAC to IP to user, regardless if you're using rotating IP's or split tunneling in your network. Our single pane of glass view immediately allows analysts to interrogate the consolidated data with exceptional pivoting, to reveal actionable intelligence. Reducing business risk in real-time, by analyzing all the data, regardless of size, allows for fast decisive action by your analyst teams.


Solution Overview
1. Emails received by Mimecast are passed through a series of hygiene scanning techniques, to ensure that they are safe before delivery to the recipient.
2. Email intelligence provided by Mimecast is sent to Fluency Security for normalization.
3. Fluency uses the email intelligence to alert analysts and add context to data from other Fluency data sources.
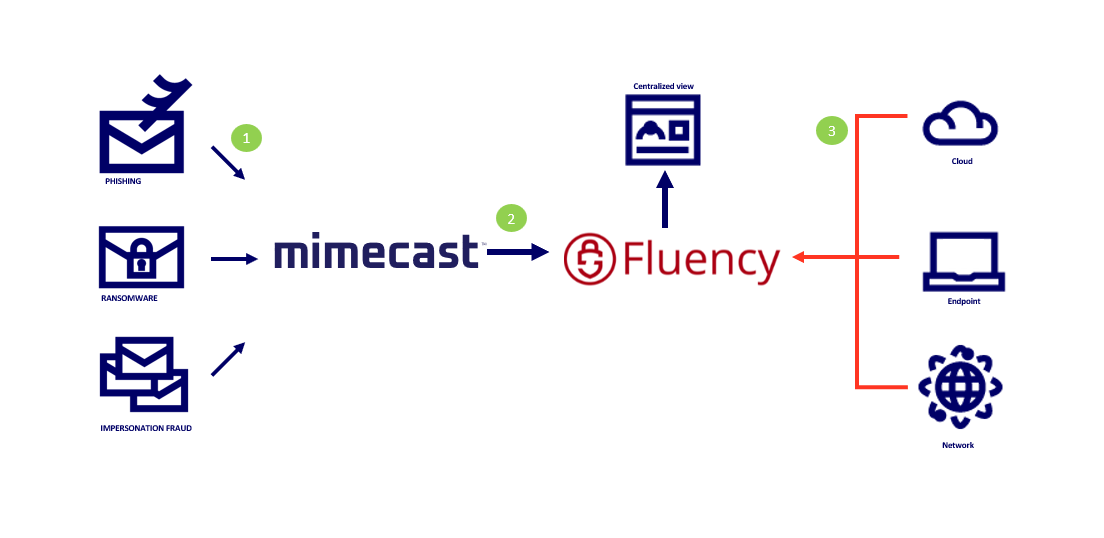
Mimecast + Fluency Security Use Cases:
Mimecast data ingested adds additional data and context within Fluency Security to aid:
Phishing

Compromised Accounts

Lateral Movement




Key Benefits
01.
Earlier detection and containment of attacks, with rapid response to phishing and business email compromise tactics.
02.
Threat intelligence enrichment detects threats within Mimecast events.
03.
Improve analysis and knowledge of threats through built in dashboards and Mimecast regional threat intelligence.
04.
Correlation across Mimecast events, cloud, endpoint, and network data to quickly identify high-risk individuals and devices that may create future security breaches.
05.
Shared intelligence identities the original threat and targets.
