HackNotice
Developed by HackNotice
Reduce third party risks by controlling communications with recently breached vendors
Mimecast and HackNotice provide a solution to optimize vendor risk management practices. By integrating Mimecast with HackNotice, security teams can leverage proactive enforcement to reduce the exposure of compromised vendor and data partner's attack campaigns. The integration offers a comprehensive solution to detect and mitigate security breaches in vendor and partner communications, preventing email-related threats such as phishing, malware, and unauthorized payments.
This integration seamlessly detects compromised domains through HackNotice and instantaneously shares this information with Mimecast. Subsequently, Mimecast blocks emails emanating from the affected domain, thwarting attacks and fraudulent before they reach employees' inboxes. By proactively shutting down the entry points used by cybercriminals sensitive data is safeguarded, operational continuity is maintained, and reputation is preserved.
Solution Overview
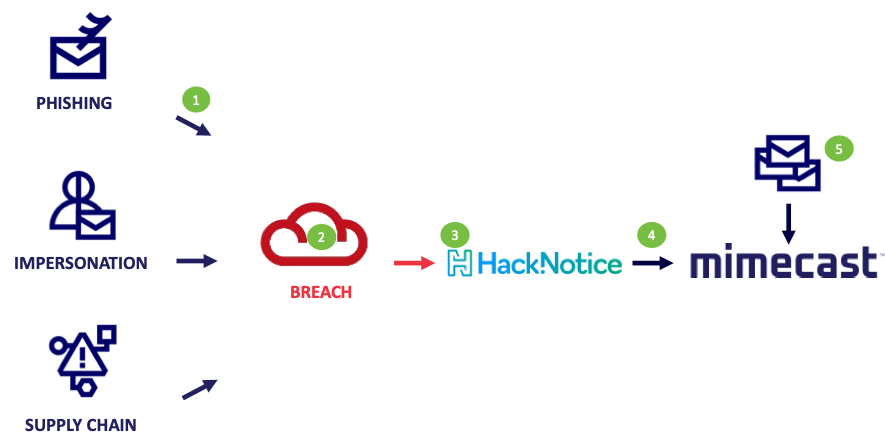
1. HackNotice searches the dark web, monitors supply chain domains and looks for account takeover indicators.
2. Phishing emails, compromised domains and corporate credentials identified in a breach are ingested by the HackNotice platform.
3. HackNotice displays the affected corporate credentials and supply chain domains to understand organizational risk.
4. Compromised domain information is sent to Mimecast which is added to a sender policy.
5. Mimecast prevents the delivery of future emails associated with the compromised domain.
Mimecast + HackNotice Use Cases:
HackNotice drives automated tasks within Mimecast based on the detection of compromised domains, harvested credentials, and dark web research increasing your security by:
- Mitigating Phishing Threats from Vendors: Protect against phishing attacks originating from compromised vendor domains
- Safeguarding Against Fraudulent Invoices from Partners: Prevent receipt of fraudulent invoices which could lead to unauthorized payments.
- Enhancing Vendor Risk Management: Proactive approach to potential security breaches safeguarding customer data, unauthorized access, and satisfying regulatory compliance.
