Coordinated, Automated, and Efficient Incident Response.
Splunk Phantom combines security infrastructure orchestration, playbook automation and case management capabilities to streamline your team, processes and tools.
Phantom’s flexible app model supports hundreds of tools and thousands of unique APIs. Codify your workflows into automated playbooks using our visual editor (no coding required) or the integrated Python development environment.


Solution Overview
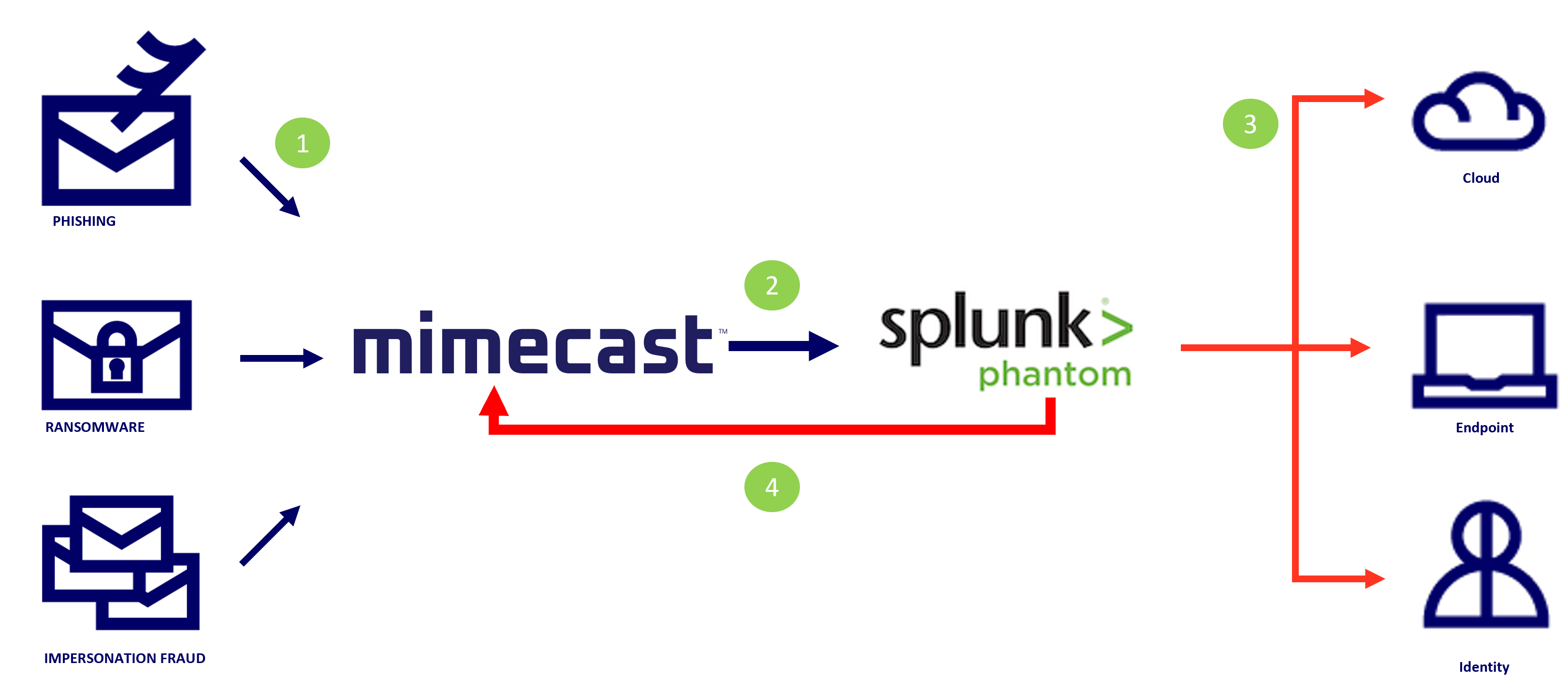
1. As inbound emails are received by Mimecast on behalf of the organization, they are subject to analysis by the Mimecast inspection funnel, where a series of email hygiene and advanced security scanning techniques are applied, to ensure that emails are safe before they are delivered to the recipient.
2. Email related data from Mimecast ingested into the Splunk Phantom platform to help with analyst investigations.
3. Coordinate response actions across security tools based on Mimecast data.
4. Adjust Mimecast policies, search and destroy malicious emails, or prevent future threats.
Mimecast and Splunk Use Cases:
Coordinated response aiding in:
Complex Email Threat Investigation

Automated Email Threat Enrichment

Complex Email Threat Investigation

Threat Intelligence





Key Benefits
01.
Automate email security processes, shorten decision making cycle, and drive resource efficiency through automation.
02.
Enrich intelligence from Mimecast and other security tools for coordinated response.
03.
Achieve full orchestration capabilities using proactive playbooks and workflows.

