Bring together the data across endpoint and email domains
API 2.0 Compatible
Easily ingest Mimecast Email Security data into CrowdStrike Falcon Next-Gen SIEM to gain comprehensive cross-domain visibility of threats throughout your attack surface. See Mimecast Email Security event data used to stop malware, spear-phishing and zero day attacks directly within the CrowdStrike Falcon platform alongside additional threat indicators from other domains to minimize context switching across multiple interfaces, allowing your team to speed up detection and triage, while improving accuracy.

Solution Overview
1. Emails received by Mimecast are passed through a series of hygiene scanning techniques, to ensure that they are safe before delivery to the recipient.
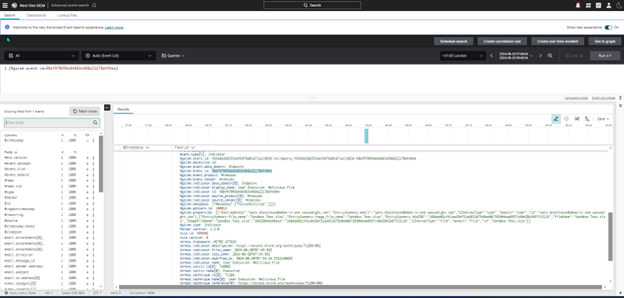
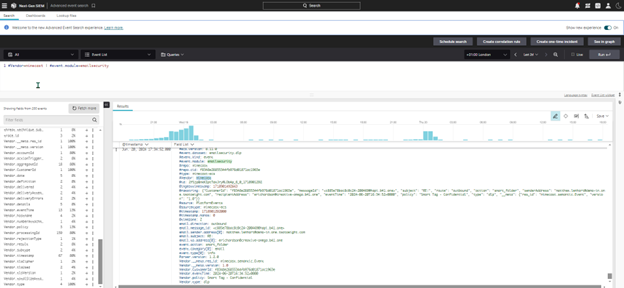
2. Email intelligence provided by Mimecast is sent to CrowdStrike Next Gen SIEM for normalization.
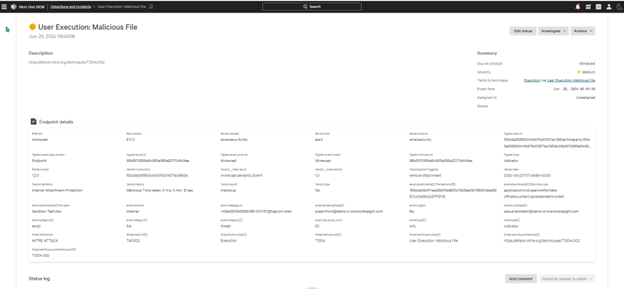
3. CrowdStrike uses the email intelligence to alert analysts and add context to data from other data sources.

Mimecast + CrowdStrike Uses Cases:
Mimecast data ingested adds additional data and context within CrowdStrike to aid:
Phishing

Compromised Accounts

Lateral Movement




Key Benefits
01.
Faster cross-domain threat detection and alerting: Get unified visibility across email and endpoint threat vectors with Mimecast email threat indicators alongside indicators from other domains within Falcon Next-Gen SIEM.
02.
Detect targeted email threats: Leverage Mimecast Email Security's visibility and intelligence of email threats with your existing CrowdStrike security data to detect whether an email message is a potential security threat
03.
Unify investigation in a single console: Save your analysts valuable time when investigating and triaging potential potential threats by minimizing context switching and accelerating threat detection through CrowdStrike's unified, threat-centric command console.
.png?rev=10bfcc4b668f482799a9efbe4e2a4253)