Enhanced protection against email-based attacks
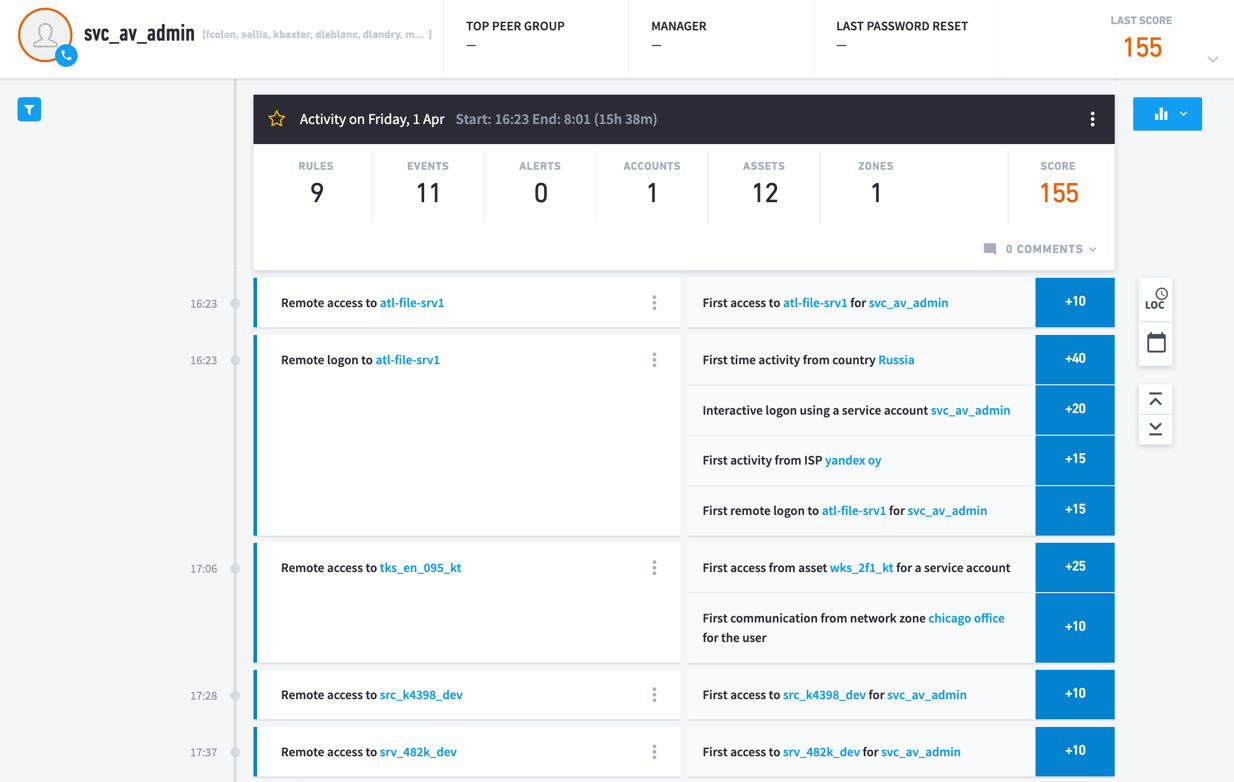
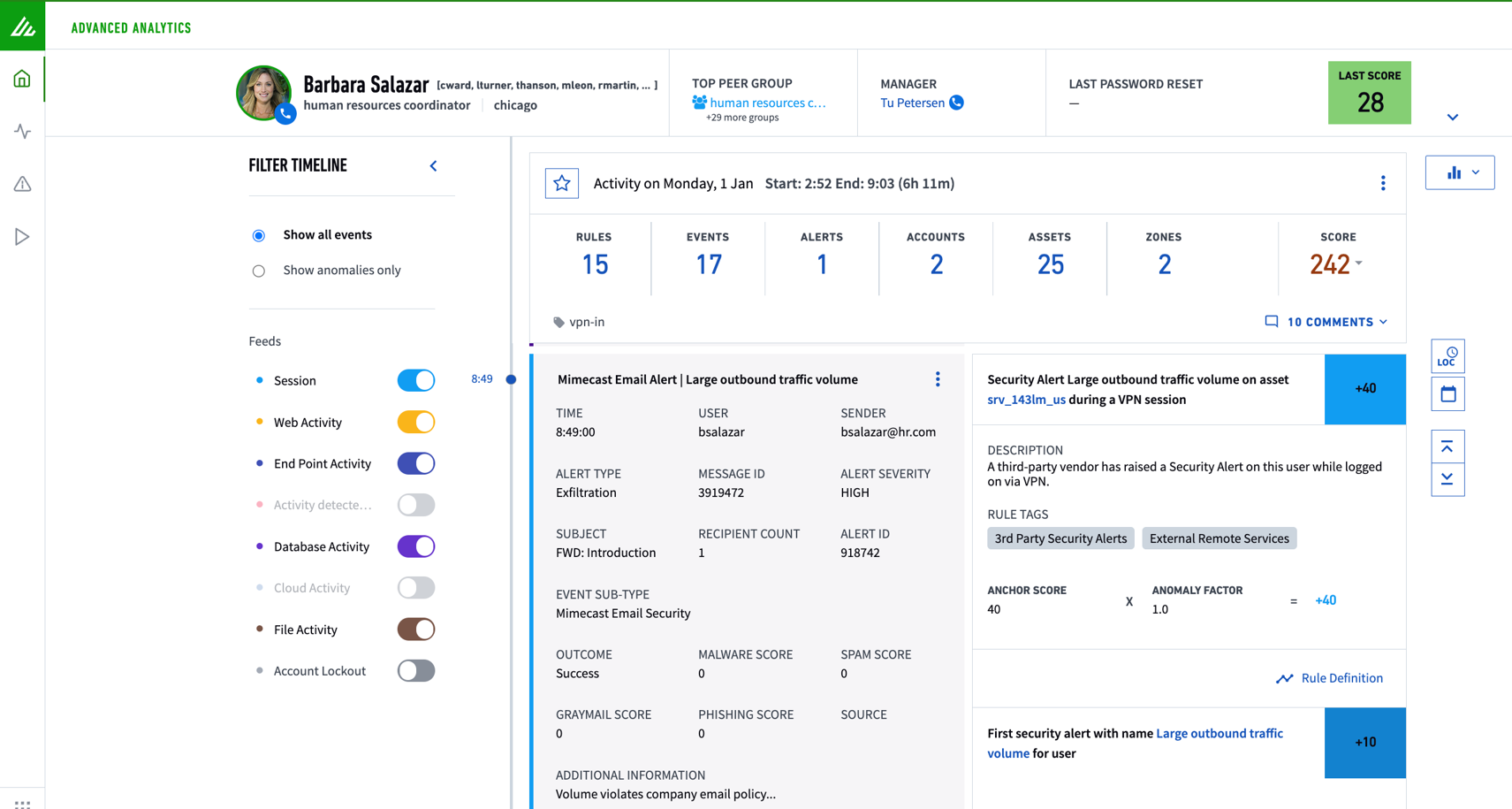
Mimecast and Exabeam provide an integrated solution to improve detection, stop threats, and provide security insights across the organization to quickly detect, investigate, and respond to cyberthreats that involve at-risk users and devices. The Exabeam integration equips security teams to better mitigate email- and credential-based attacks. When combining Mimecast log data with Exabeam Security Analytics, customers can baseline normal activity for all users and entities. Security teams can visualize all notable events within a contextualized, automated Smart Timeline™, streamlining investigations and eliminating hundreds of analyst queries. This enables security teams to prevent initial infection and mitigate lateral spread that can lead to downtime, ransom demands, data loss, and stolen passwords.

Solution Overview
1. As inbound emails are received by Mimecast on behalf of the organization, they are subject to analysis by the Mimecast inspection funnel, where a series of email hygiene and advanced security scanning techniques are applied, to ensure that emails are safe before they are delivered to the recipient.
2. Email intelligence produced by Mimecast is sent to Exabeam.
3. Exabeam adds context to data from other sources and alerts analysts.
4. Playbooks run corrective actions within Mimecast and other security tools.

Flexible Integration Actions
Mimecast + Exabeam Use Cases
Mimecast and Exabeam share high-fidelity indicators and remediation actions to support:
Detect and Contain Attacks Earlier

Enrich Threat Detection
Utilizing Mimecast events with Exabeam analytics and threat intelligence
Increase protection, reduce resource utilization, and improve analysis and knowledge of threats
Utilize built-in dashboards and Mimecast regional threat intelligence

Key Benefits
01.
Earlier detection and containment of attacks, with rapid response to phishing and business email compromise tactics.
02.
Exabeam analytics and threat intelligence enrichment detects threats within Mimecast events.
03.
Increase protection, reduce resource utilization, and improve analysis and knowledge of threats through built in dashboards and Mimecast regional threat intelligence.
04.
Correlation across Mimecast events, cloud, endpoint, and network data to quickly identify high-risk individuals and devices that may create future security breaches.