Security Insights for Proactive Detection
By integrating Mimecast with Trellix ESM, organizations can analyze and investigate reported phishing attempts in minutes - stopping attacks before malicious actors can gain momentum in the network. Security teams can save time by accelerating the onboarding process, leveraging an intuitive dashboard to cut cyber attack detection time, and full visibility into the kill chain for proactive response.


Solution Overview
1. Emails received by Mimecast are passed through a series of hygiene scanning techniques, to ensure that they are safe before delivery to the recipient.
2. Email intelligence provided by Mimecast is sent to Trellix for normalization.
3. Trellix uses the email intelligence to alert analysts and add context to data from other sources.
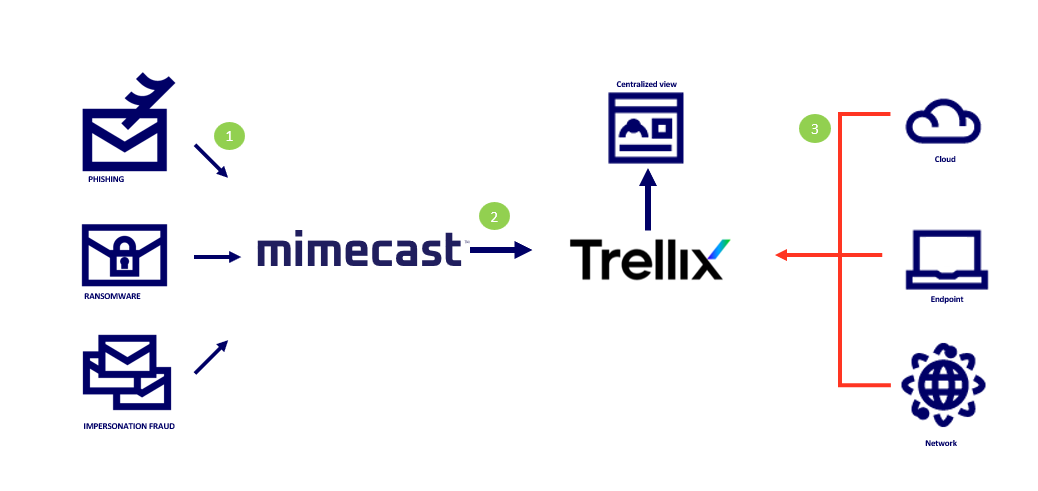
Mimecast + Trellix Use Cases:
Mimecast data ingested adds additional data and context within Trellix ESM to aid:
Phishing

Compromised Accounts

Lateral Movement




Key Benefits
01.
Improve Visibility - Gain visibility into threats that start with email.
02.
Enhance Intelligence - Correlate email-borne attacks with events observed in other security systems and leverage McAfee ESM advanced analytics to help detect and prioritize threats.
03.
Get ahead of attacks - Use email activity data to spot anomalies that could be a leading indicator of an attack.
